Table of Contents
Today we’re looking at the best cybersecurity books of this year.
🧠 Did you know? According to Cybint, there’s been a 300% increase in reported cyber crimes since COVID-19.
What is cybersecurity?
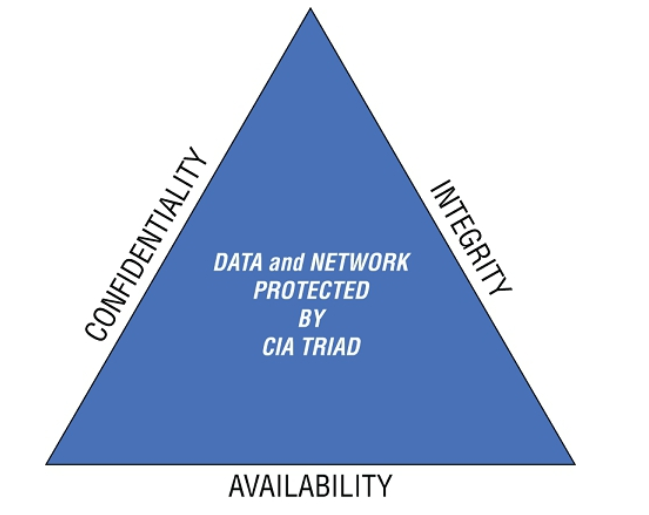
Cyber attacks typically target sensitive information to access, change or destroy it. Cybersecurity is the protection of computer systems and networks from these digital attacks.
This post contains affiliate links. I may receive compensation if you buy something. Read my disclosure for more details.
TLDR: Best Cybersecurity Books This Year
🔥 Best Overall 🔥
Cybersecurity Ops with bash
💥 Best for Newbies 💥
How Cybersecurity Really Works: A Hands-On Guide for Total Beginners
💸 Best Value 💸
Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World
Best Cybersecurity Books
Now let’s dive into some of the best cybersecurity books of this year.
You’ll discover their:
- features
- core concepts
- layout
- comparisons
And more.
1. Cybersecurity Ops with bash: Attack, Defend, and Analyze from the Command Line
↘️ Ideal for: students, security practitioners, administrators
↘️ Topics covered: defensive security, penetration testing, security administration
Cybersecurity Ops with bash is a practical guide that shows you how to attack and defend from the command line.
➡️ Cybersecurity Ops with bash is one of the best cybersecurity books overall.
It shows you how to use the command line interface (CLI) and bash shell to perform tasks like:
✅ data collection and analysis
✅ intrusion detection
✅ reverse engineering
And administration.
The book is divided into four sections where you’ll learn the tools and techniques to monitor network:
1️⃣ foundations
2️⃣ defensive security operations
4️⃣ security administration
And more.
Bill found Cybersecurity Ops with bash to be incredibly helpful:
The authors have done a commendable job discussing and exploring the powerful capabilities buried in the command line language BASH.
– Bill
📣 Start your ethical hacking adventure with the video course Complete Ethical Hacking Bootcamp on Zero to Mastery.
2. How Cybersecurity Really Works: A Hands-On Guide for Total Beginners
↘️ Ideal for: students, business professionals
↘️ Topics covered: tactics and defense strategies
How Cybersecurity Really Works is similar to Cybersecurity Ops with bash.
But this guide to hacking basics is a little more beginner-friendly.
➡️ How Cybersecurity Really Works is one of the best cybersecurity books for students.
You’ll learn how to navigate:
✅ types of attacks
✅ tactics used by black hat hackers
✅ defensive strategies
And beyond.
With real-world examples and hands-on exercises, you’ll:
✅ analyze emails to detect phishing
✅ use SQL injection to attack a website
✅ use the command line to improve security
✅ create a risk management plan
And much more.
In all, How Cybersecurity Really Works teaches you how to implement cybersecurity measures on your devices.
📣 Discover the exciting world of bug bounty hunting in the course Web Security & Bug Bounty: Learn Penetration Testing on Zero to Mastery.
3. Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World
↘️ Ideal for: industry newbies, corporate climbers, consultants
↘️ Topics covered: cybersecurity misconceptions, cybersecurity credentials
Tribe of Hackers is different than Cybersecurity Ops with bash and How Cybersecurity Really Works.
Rather than learn the technical aspects of cybersecurity, you’ll find 70 interviews from cybersecurity experts.
➡️ Tribe of Hackers is one of the best cybersecurity books for students who want to learn from some of the world’s most notable hackers.
You’ll learn about:
✅ cybersecurity myths and misconceptions
✅ credentials you need for cybersecurity
✅ how social media and IoT has changed cybersecurity
And more.

📣 Take a journey into ethical hacking in the course Learn Ethical Hacking From Scratch on BitDegree.
4. Cybersecurity and Cyberwar: What Everyone Needs to Know
↘️ Ideal for: beginners and experienced cybersecurity experts
↘️ Topics covered: how cybersecurity works, Anonymous, Stuxnet
Cybersecurity and Cyberwar is an easy-to-read manual using stories and anecdotes.
➡️ We think Cybersecurity and Cyberwar is one of those must-have cybersecurity books.
It answers some of the most pressing questions about cybersecurity such as:
✅ how it works
✅ why it matters
✅ what we can do
The book uses examples such as the Anonymous hacker group and the Stuxnet computer virus.
What cybersecurity students are saying about Cybersecurity and Cyberwar:
Anyone entering the cybersecurity field should read this book.
– Tiny
📣 Learn best cybersecurity practices in the course Practical Security: Simple Practices for Defending Your Systems on Educative.io.
5. Network Security Assessment: Know Your Network
↘️ Ideal for: beginners
↘️ Topics covered: vulnerabilities, techniques, countermeasures
Network Security Assessment explores how to perform network-based penetration testing.
➡️ Network Security Assessment is one of the best cybersecurity books showing you how to discover system vulnerabilities by attacking your own system.
First you’ll learn about common vulnerabilities.
Then you’ll discover attacker techniques and how to mitigate them.
Finally, you’ll explore how to test system components such as:
✅ Microsoft services
✅ TLS protocols
✅ Web server software
✅ database servers
✅ frameworks
And much more.
📣 Learn all about cybersecurity basics in the course Introduction to Cybersecurity Tools & Cyber Attacks on Coursera.
6. Cybersecurity Incident Management Masters Guide
↘️ Ideal for: beginners and experienced cybersecurity experts
↘️ Topics covered: incident management
Cybersecurity Incident Management teaches you how to respond to cybersecurity threats using a well-planned and organized incident management program.
➡️ Cybersecurity Incident Management Masters Guide is one of the best cybersecurity books showing you how to be effective against most known and newly evolved cyber threats.
You’ll learn how to navigate the latest threats while examining:
✅ security controls
✅ regulatory requirements
✅ customer environment
✅ threat landscape
Developed over two decades, this incident management program will guide you through the incident response lifecycle.

📣 For a short introduction to ethical hacking, check out the course Ethical Hacking: System Hacking on Pluralsight.
7. How to Measure Anything in Cybersecurity Risk
↘️ Ideal for: cybersecurity newbies
↘️ Topics covered: risk management approaches, methods
How to Measure Anything in Cybersecurity Risk takes a different approach to cybersecurity.
Rather than point out best practices and risk management, you’ll find their shortcomings. Then you’ll learn how to patch these holes and increase your security.
➡️ How to Measure Anything in Cybersecurity Risk is one of the best cybersecurity books for learning quantitative processes and techniques.
In fact, it will steer you away from dangerous risk management methods. And instead leave you with powerful protection.
8. Cybersecurity and Third-Party Risk: Third Party Threat Hunting
↘️ Ideal for: beginner to intermediate cybersecurity practitioners
↘️ Topics covered: third-party risk management fundamentals, on-site due diligence, software supply chain security
Cybersecurity & Third-Party Risk teaches you how to squash vulnerabilities created by third parties.
➡️ Cybersecurity and Third-Party Risk will show you how to strengthen the weakest links in your cybersecurity chain.
Instead of a low-level checklist, you’ll create an active system of third-party cybersecurity risk minimization by practicing:
✅ third-party risk management fundamentals
✅ due diligence
✅ securing your software supply chain
✅ monitoring third-party vendors
And much more.
9. Cybersecurity – Attack and Defense Strategies
↘️ Ideal for: penetration testers, security consultants, ethical hackers
↘️ Topics covered: security foundations, policies, security monitoring
Cybersecurity – Attack and Defense Strategies is for IT professionals looking for the latest techniques and skills for threat hunting.
➡️ Cybersecurity – Attack and Defense Strategies is ideal for cybersecurity professionals who want to understand cyber attacks through the lens of the attacker.
Going into the mind of a Threat Actor, you’ll learn how systems become compromised and how to exploit vulnerabilities in your own system.
You’ll also explore:
✅ attack strategy
✅ cyber resilience
✅ defense tools
✅ types of cyber attacks
✅ the disaster recovery process
And beyond.
10. Cybersecurity: The Insights You Need from Harvard Business Review
↘️ Ideal for: companies, individuals
↘️ Topics covered: cybersecurity, case studies, hacking prevention
Cybersecurity: The Insights you Need covers cybersecurity foundations with practical case studies.
➡️ Cybersecurity: The Insights You Need from Harvard Business Review features cybersecurity precautions you can take to avoid becoming a hacking victim.
Looking into data security practices and identifying suspicious activity, you’ll gain the necessary insight to prepare for an inevitable hacking attempt.
11. Cybersecurity Blue Team Toolkit
↘️ Ideal for: IT security professionals, technical analysts, program managers
↘️ Topics covered: best practices, security assessment, defense strategies
Cybersecurity Blue Team Toolkit has a useful blend of technical and non-technical aspects of cybersecurity to keep readers of all levels engaged.
➡️ Cybersecurity Blue Team Toolkit was created by a former Department of Defense employee.
While using best practices and tools, you’ll discover:
✅ security assessment
✅ protection strategies
✅ offensive measures
✅ remediation
And beyond.
12. Cybersecurity: The Beginner’s Guide
↘️ Ideal for: cybersecurity newbies
↘️ Topics covered: security certifications, practice labs
Cybersecurity: The Beginner’s Guide is a hands-on approach to transitioning into the field of cybersecurity.
➡️ Cybersecurity: The Beginner’s Guide is one of the best cybersecurity books for beginners looking to transition into the field of cybersecurity.
In addition to practice labs, you’ll explore real-world use cases.
You’ll also become familiar with security certifications.
13. Cybersecurity Essentials
↘️ Ideal for: cybersecurity newbies
↘️ Topics covered: fundamentals, defense, protocols
Cybersecurity Essentials is a comprehensive introduction to cybersecurity.
➡️ Cybersecurity Essentials is one of the best cybersecurity books for learning the basics of cybersecurity.
Here you’ll discover effective defense methods such as securing:
✅ infrastructure
✅ devices
✅ local networks
✅ the perimeter
You’ll find plenty of real-world scenarios and hands-on exercises.
14. Cybersecurity for Beginners
↘️ Ideal for: non-technical newbies
↘️ Topics covered: risks, technical terms, the cloud
Cybersecurity for Beginners takes a non-technical approach to cybersecurity.
➡️ Cybersecurity for Beginners is one of the best cybersecurity books for non-technical newbies.
You’ll discover the importance of companies using cybersecurity in today’s technological landscape.
In addition, you’ll explore the risks associated with the cloud and smart devices.
15. Cybersecurity Resilience Planning Handbook
↘️ Ideal for: executive & IT management, security administrators
↘️ Topics covered: cyber threats, building resilient systems
The Cybersecurity Resilience Planning Handbook helps you identify cyber threats and build resilient, secure systems.
➡️ Cybersecurity Resilience Planning Handbook is one of the best cybersecurity books you’ll find for high-level system defense.
There are over 150 workflow tools including:
✅ risk assessment worksheets
✅ forms
✅ checklists
✅ policies
With these tools, you can improve your cybersecurity program and stop cyber threats in their tracks.
Best Cybersecurity Books: Conclusion
Let’s recap what we’ve looked at today.
Today we showed you the best cybersecurity books including:
🔥 Best Overall 🔥
Cybersecurity Ops with bash
💥 Best for Newbies 💥
How Cybersecurity Really Works: A Hands-On Guide for Total Beginners
💸 Best Value 💸
Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World
So whether you’re a total newbie or are looking to improve your cybersecurity skills, we think there are cybersecurity books for just about everyone.
Cybersecurity buffs are also reading:
- 6 Best Cybersecurity Courses You Need
- 9 Best Hacking Courses & Books for This Year
- 13 Best Cryptography Books
- 11 Best IoT Books
What is cybersecurity?
Cyber attacks typically target sensitive information to access, change or destroy it. Cybersecurity is the protection of computer systems and networks from these digital attacks. You can learn more about cybersecurity in today’s post.
What are the best cybersecurity books?
Overall, we think Cybersecurity Ops with bash is the best cybersecurity book. For newbies, we liked How Cybersecurity Really Works: A Hands-On Guide for Total Beginners. And for value, we chose Tribe of Hackers: Cybersecurity Advice from the best hackers in the world. Check out today’s post where we look at these and other cybersecurity books.
Are there cybersecurity courses?
Yes, there are cybersecurity courses. You’ll find these cybersecurity courses on a number of platforms including Zero to Mastery, Educative.io, BitDegree and Pluralsight. Learn more about these courses in today’s post.
What’s the difference between hacking and cybersecurity?
In cybersecurity, you defend systems from malicious attacks. Hackers take a more proactive approach by exploiting system vulnerabilities. Discover more on cybersecurity in today’s post where we examine the best cybersecurity books.
Is cybersecurity worth it?
We certainly think so. With thousands of job vacancies, generous compensation packages and a challenging work environment, cybersecurity can prove to be a lucrative career. Learn more about the benefits of cybersecurity in today’s article.















